Introduction to Application Pool
Application Pools are logical groupings of web applications that will execute in a common process, thereby allowing greater granularity of which programs are grouped together in a single process. For instance, if you wanted every Web Application to execute in a separate process, you simply create an Application Pool for each application. The Application Pool is the heart of a website. Application Pools enable us to isolate our Web Application for better security, reliability and availability. The worker process serves as the process boundary that separates each Application Pool so that when a worker process or application is having an issue or recycles, other applications or worker processes are not affected.

The maximum number of Application Pools that is supported by IIS is 2000.
Introduction to Web Garden
An Application Pool with multiple worker processes is called a Web Garden. Many worker processes with the same Application Pool can sometimes provide better throughput performance and application response time.

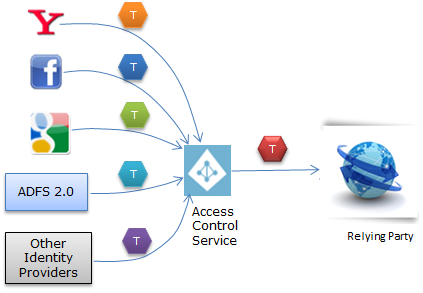
A Web Garden is a site configured to run within multiple processes on a single server. You can still have multiple servers configured in a web farm, but the Web Garden reflects the configuration of a specific individual server. Now I am explaining how to deploy a Web Site on IIS.
How to Deploy site on IIS
I had generated my code and before deploying on IIS it is running in the browser like this:

And I will deploy on IIS. There are 2 ways:
Application Pools are logical groupings of web applications that will execute in a common process, thereby allowing greater granularity of which programs are grouped together in a single process. For instance, if you wanted every Web Application to execute in a separate process, you simply create an Application Pool for each application. The Application Pool is the heart of a website. Application Pools enable us to isolate our Web Application for better security, reliability and availability. The worker process serves as the process boundary that separates each Application Pool so that when a worker process or application is having an issue or recycles, other applications or worker processes are not affected.

The maximum number of Application Pools that is supported by IIS is 2000.
Introduction to Web Garden
An Application Pool with multiple worker processes is called a Web Garden. Many worker processes with the same Application Pool can sometimes provide better throughput performance and application response time.

A Web Garden is a site configured to run within multiple processes on a single server. You can still have multiple servers configured in a web farm, but the Web Garden reflects the configuration of a specific individual server. Now I am explaining how to deploy a Web Site on IIS.
How to Deploy site on IIS
I had generated my code and before deploying on IIS it is running in the browser like this:

And I will deploy on IIS. There are 2 ways:
- Within the Visual Studio
- From IIS itself
1. Within the Visual Studio
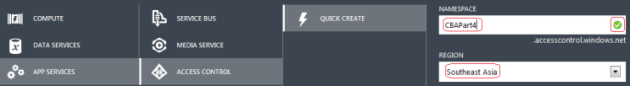
Step 1: Go to Solution Explorer and select Web Application < Properties.

Step 2: Go to the Web tab and provide the name of the virtual directory.

After clicking it will show the message.

Output: Now the URL will change.

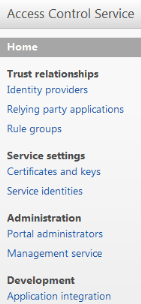
Open IIS within the run window and type inetmgr.

2. From IIS itself
Now delete the previous application from the IIS.

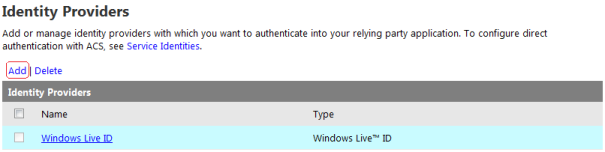
Step 1: Now go to the Default Web Site then Add Application and here provide the alias name and select the Application Pool name and provide the physical path of the Web Application.


Now, I can still access this Web Application with the same name.

All the applications present in the Application Pool can be in the same Application Pool or may be in a different Application Pool.
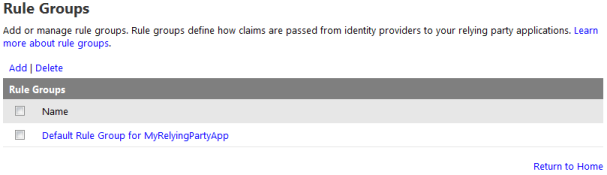
How to create an Application Pool
To create an Application Pool click on Application Pools < Add Application Pool.

Provide the name of Application Pool and select the version of the .Net Framework and click OK.

There are 0 applications and each Application Pool has its own worker process.
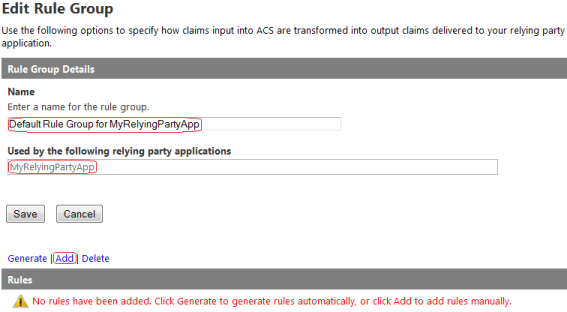
Application Pool identity
The identity of an Application Pool is the name of the service account under where the Application Pool's worker process runs and it depends on the identity setting of the Application Pool.
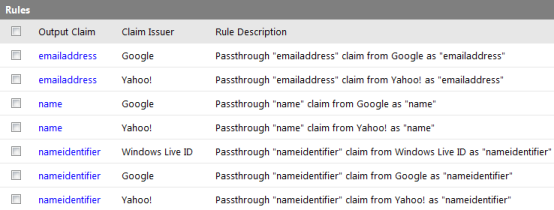
Now go to Application Pool and right-click on Advanced Settings.

Click on the ApplicationPoolIdentity and here there is built- in account and they have a different property for security purposes and by default it is the ApplicationPoolIdentity account in IIS 7.

We can set the Custom account also by giving the user name and password.

Now, I am explaining Application Pool identities:
Step 1: Go to Solution Explorer and select Web Application < Properties.

Step 2: Go to the Web tab and provide the name of the virtual directory.

After clicking it will show the message.

Output: Now the URL will change.

Open IIS within the run window and type inetmgr.

2. From IIS itself
Now delete the previous application from the IIS.

Step 1: Now go to the Default Web Site then Add Application and here provide the alias name and select the Application Pool name and provide the physical path of the Web Application.


Now, I can still access this Web Application with the same name.

All the applications present in the Application Pool can be in the same Application Pool or may be in a different Application Pool.
How to create an Application Pool
To create an Application Pool click on Application Pools < Add Application Pool.

Provide the name of Application Pool and select the version of the .Net Framework and click OK.

There are 0 applications and each Application Pool has its own worker process.
Application Pool identity
The identity of an Application Pool is the name of the service account under where the Application Pool's worker process runs and it depends on the identity setting of the Application Pool.
Now go to Application Pool and right-click on Advanced Settings.

Click on the ApplicationPoolIdentity and here there is built- in account and they have a different property for security purposes and by default it is the ApplicationPoolIdentity account in IIS 7.

We can set the Custom account also by giving the user name and password.

Now, I am explaining Application Pool identities:
Built-in user account: This are the 4 types of built-in user accounts.
- Local System: It is part of the Administrators group on the Web server. It is a completely trusted account and has very high privileges and can also access network resources.
- Network Service: This is the Restricted or limited service account that is generally used to run and this account provides the most security against an attack that might try to take over the web server.
- Local Services: It's the same as network services and it does not access network resources.
- ApplicationPoolidentity: Starting with IIS 7, Application Pools can be ran as the "ApplicationPoolIdentity" account. This is a dedicated pseudo user account for the working process of an Application Pool and is the recommended pool identity.
Custom user account
- Installed user account: You can configure an installed User Account under which you want the worker process to run.
- Property-based user: You can dynamically choose a username and a password under which you want the
worker process to run. - Password property: The password is stored inside a property.
- Predefined password: By selecting this option you can define your own password.
A custom account is useful in the following situations:
- Want more security.
- When you are hosting web sites for multiple customers on a single web server. If you use the same process account for multiple customers, the source code from one customer's application may be able to access source code from another customer's application. In this case, you should also configure a custom account for the anonymous user account.
- When an application requires rights or permissions in addition to the default permissions for an Application Pool.
How to associate a Web Application with an Application Pool
Now go to Web Application < Manage Application < Advanced Settings.

And here select the Application Pool that you want and I have selected my own Application Pool "myappPool".

Now here go to Application Pool and there is one Web Application.
Advantage of Application Pool
Now go to Web Application < Manage Application < Advanced Settings.

And here select the Application Pool that you want and I have selected my own Application Pool "myappPool".

Now here go to Application Pool and there is one Web Application.
Advantage of Application Pool
- If we deploy an application in one worker process and it is running and another Application Pool's Web Application is also running and if it has any other problem then it will not be affected by other Application Pool's Web Application.
- Deploying an applications to multiple Application Pools enable us to achieve the degree of application isolation that we need, in terms of availability and security.